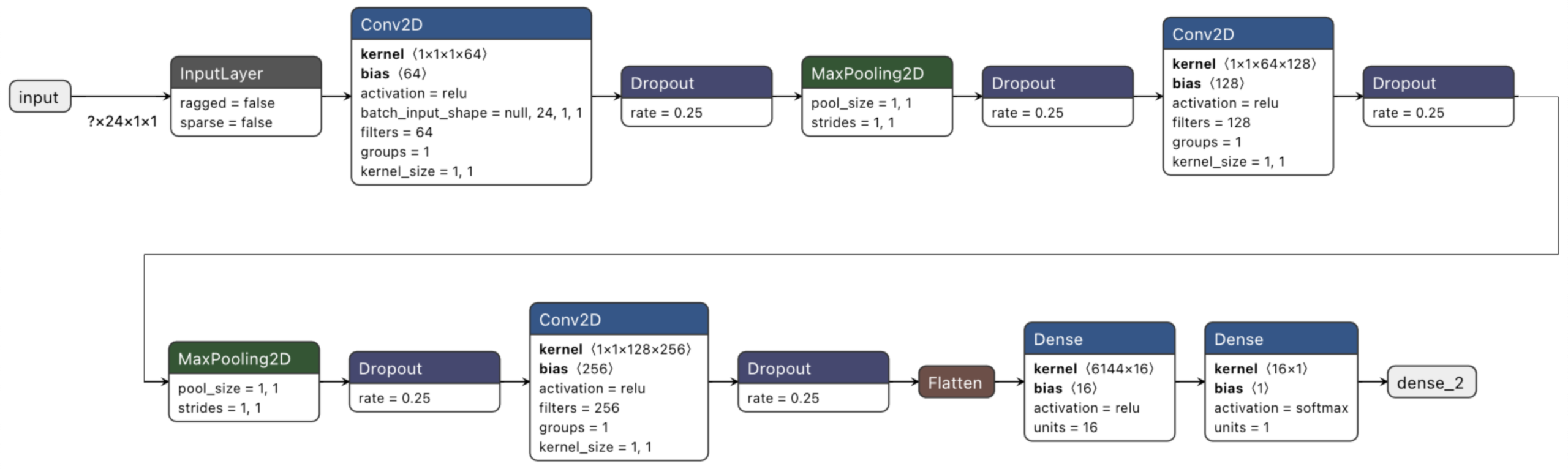
Software-Defined Networking (SDN) is a new paradigm that revolutionizes the idea of a software-driven network through the separation of control and data planes. It addresses the problems of traditional network architecture. Nevertheless, this brilliant architecture is exposed to several security …
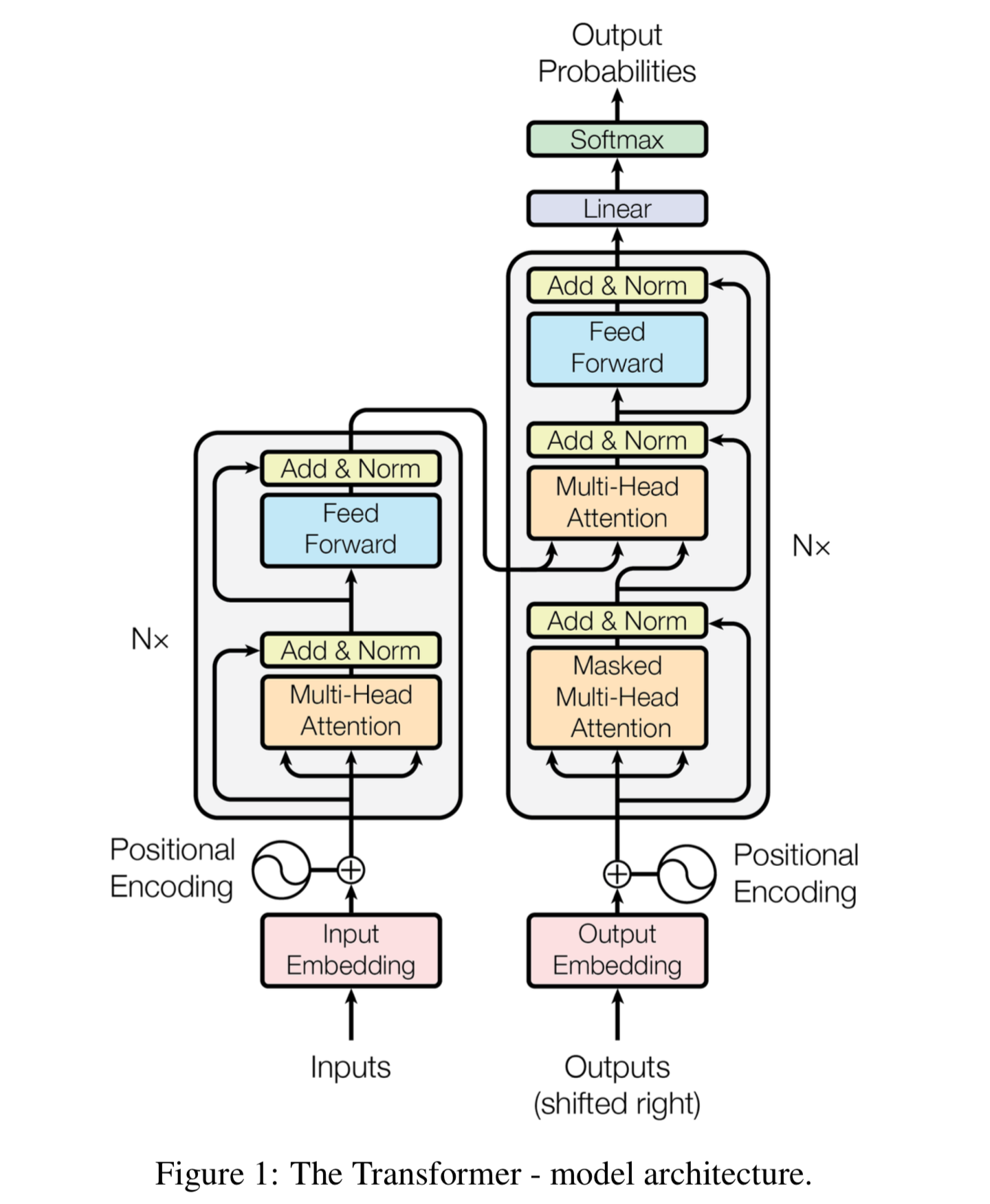
We cannot overemphasize the essence of contextual information in most natural language processing (NLP) applications. The extraction of context yields significant improvements in many NLP tasks, including emotion recognition from texts. The paper discusses transformer-based models for NLP tasks. It …
Connected Devices Lab in December 2020, participated and presented three accepted papers the 2020 17th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP). The conference was held at the University of Electronic Science and Technology of …
Emotion detection (ED) is a branch of sentiment analysis that deals with the extraction and analysis of emotions. The evolution of Web 2.0 has put text mining and analysis at the frontiers of organizational success. It helps service providers provide …
The high possibility of attack is greatly attributed to the broadcast nature of the communication medium in which the sensor nodes operate; this makes eavesdropping of messages possible on the network. This paper proposes a privacy-aware sociopsychological trust and reputation …
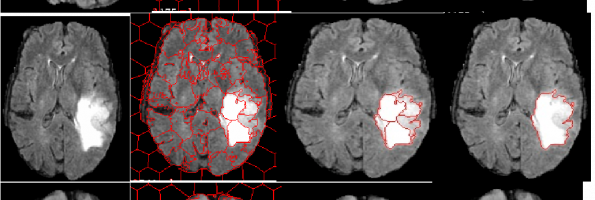
This paper deals with the implementation of a simple algorithm for automatic brain tumor segmentation. Brain tumor is commonly diagnosed by Computer tomography and Magnetic Resonance Imaging in clinical treatment. The paper uses Simple Linear Iterative Clustering (SLIC) to segment …
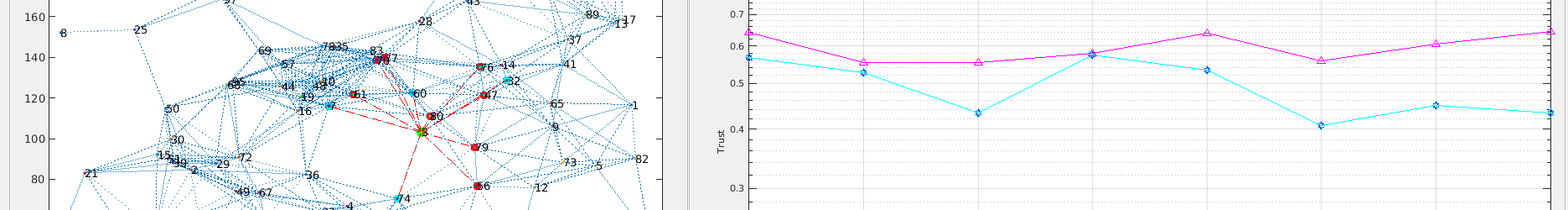
SoTRMSim is a MATLAB based simulator for simulating Wireless Sensor Networks (WSN) utilised in computing sociopsychological trust and reputation models. You can also use it to build randomised network deployments for other WSN related research work. This is ideal for …
The security of a wireless sensor network is greatly increased with increasing levels of trustworthiness of nodes on the network. There are a number of trust models proposed that use various trust evaluation methods. The paper categorises trust evaluation methods …
Paper Abstract Sensor nodes once deployed onto the field are mostly provided with little or no attention making them prone to physical attacks by adversaries. Various security frameworks have been proposed to mitigate tampering; others also ensure authentication of sensor …