The Human Errors that Defeated Enigma
Recently, when researchers at the University of Rochester (USA) finally succeeded in developing a totally secure encryption device based on quantum rules, they presented it as the “Quantum Enigma†in honour of the rotor cipher machines used to encode Nazi messages in the Second World War, the same devices that continue breaking records at auctions today. Why is an ingenious mechanism from a century ago still so fascinating?
Beyond its history and the feat of its decipherment by the British cryptanalysts of Bletchley Park—with Alan Turing leading—the key must be sought in the incredible level of impregnability achieved by the Enigma. The machine invented in 1918 by the German engineer Arthur Scherbius consisted basically of three components connected by wires: a keyboard to introduce the original message, a modifying unit, and a panel with lamps where the corresponding letter of the encrypted message was illuminated.
The fundamental part was the modifying unit, responsible for the coding process, and integrated by three types of components: plugboard, rotors and reflector.

During World War II, the Germans used the Enigma machine to develop nearly unbreakable codes for sending messages. Credit: Greg Goebel
The Enigma had three rotors, connected in series. They were thick discs, each with 26 input points (one for each letter of the alphabet) and as many output points. The internal wiring, different on each disk, made the signal that entered from one position exit from a different one: it was rerouted by turning it into another letter. In addition, each rotor automatically rotated at a certain rate. The first rotor rotated one position each time a letter was pressed from the original message. The second rotor advanced one position each time the first rotor completed one full turn, and the third did the same when the second was completed.
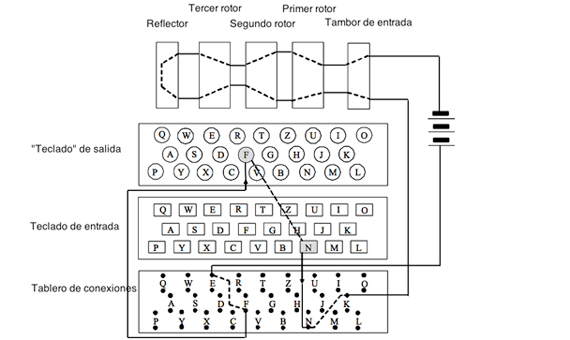
Diagram showing the operation of the Enigma encryption machine. Credit: Cryptomuseum
It is easy to visualize if you think of a clock of needles. With each push of the mechanism, the second hand advances one position. When you complete a whole lap, the minute hand moves forward. And only when it completes a turn does the hour hand advance a position. It takes 12 hours for two similar needle arrangements to occur. In other words, there are 60 x 60 x 12 = 43,200 combinations or arrangements of the different needles. If this is transferred to a three-disc system (with 26 positions each) you have 26 x 26 x 26 = 17,576 different arrangements. This means that when the operator types a letter it can be coded according to any of the tens of thousands of possible configurations (equivalent to different encrypted alphabets). And then the arrangement changes and the next letter is already encoded through a different layout/alphabet.
Trillions of possible configurations
The reflector is another type of disk with internal wiring, but it does not rotate and the wires enter and leave on the same side, though in different positions. It is located next to the rotors. Thus, by typing one letter of the original message, the electric signal passes through the rotors, enters the reflector and then exits it, travelling back through the three modifiers but by a different route to reach the panel. Its usefulness, beyond multiplying the number of configurations, is that it automates the decryption process. Thanks to the reflector, the encoding and decoding processes are self-reciprocal, meaning that they are reflections of each other. Therefore, in order to decrypt a message, the receiver only needs to have another Enigma machine in the same starting position and then by typing the encrypted message the original will appear.

Rotors with alphabet rings in an Enigma machine. Credit: TedColes
Finally, the plugboard is fixed panel located just in front of the rotors that allows the operator to insert cables that have the effect of exchanging some letters before they access the modifier. The Enigma had six cables with which six pairs of letters could be exchanged. The number of ways to connect six pairs of letters out of 26 is 100,391,791,500, which multiply the 17,576 rotor arrangements.
Scherbius decided to further increase the level of security in the coding of his machine. He could have increased the number of rotors in series, but the machine would have been too big and not operational from a military point of view. Instead, he opted for them to be interchangeable. On each occasion they were arranged in a different and “random†order in the machine (1-2-3, 1-3-2, 2-1-3, 2-3-1, 3-1-2 or 3-2-1). In total there were six possible orders, which multiply the previous arrangements to give approximately 10 billion trillion possible configurations. This datum gives us some perspective on the security level of the encoding and the difficulty of its decryption. In 1926, the German army began to use the Enigma 1.
Keeping secret the initial conditions
Beyond its design, the impregnability of the Enigma depended on keeping secret the initial conditions: the starting position of the rotors and the cabling of the plugboard. If one knows the initial conditions, one need only type the coded message into the device to obtain the original, but without them, the only thing that the machine is worth is for trying the trillions of possible configurations.
It was therefore necessary to periodically distribute to all the German army operators a “daily key setting†booklet which included the initial conditions for each day and which listed the order in which the three rotors were placed in the machine, the initial position of each of them and the position of the cables of the plugboard.
In order to prevent all the communications of the day being encrypted by the same key—the greater the number of messages encoded with the same key, the more likely it is to be deciphered—the Germans decided to use the “daily key setting†only to encode a “message key†with which they began each of their messages and which varied from one to another.
The sender chooses a random arrangement of the rotors, which would be the “message keyâ€, transmits it encoded with the “key of the day†and then sends the message encrypted according to the new key. The receiver, who has his Enigma arranged according to the “key of the day†receives the message and knows that the first three letters correspond to the “message keyâ€, that is to say, to the new arrangement of the rotors (the position of the cables in the plugboard and the order of the rotors indicated by the “conditions of the dayâ€). Then he readjusts the position of the rotors and decrypts the rest of the message.
This is a system that is seemingly impossible to overcome except for the fact that the German operators, in order to avoid errors in the reception, decided to type the “message key†twice in a row, and that introduced a weakness into the system. Thereafter, the 1st and 4th letters, 2nd and 5th and 3rd and 6th of each intercepted message were encryptions of the same letter.
Deciphering the German communications
That minimal information and a replica of the Enigma machine obtained by the spy services were all that the Polish mathematician Marian Rejewski needed in 1932 to decipher the German communications.
Because in spite of everything, both the Polish cryptanalysts and later their English colleagues managed to find a vulnerability in the Enigma machine and defeat it, a defeat that was more attributable to the procedural flaws and mistakes of the operators who handled it than to the machine per se.
In 1938, the Germans decided to recover the security of the Enigma. Each operator would have a set of five rotors from which the three that were mounted in the machine were chosen, and the number of cables in the plugboard was increased from 6 to 10. The possible configurations now amounted to 159 trillion. When the war broke out, the number of rotors in the Enigma machines of the Kriegsmarine, the German navy, expanded from 5 to 8. The Enigma was once again impregnable.
On July 24, 1939, before the start of the Nazi invasion of Poland, the head of the Polish secret service informed his British counterparts of their achievements and gave them a replica of the Enigma in the hope that, with more time and resources, they would be able to break it again. And they did. Their success was based on the visionary talent of Alan Turing, but also on the cracks that the German operators opened in the impenetrability of the Enigma.
There were human errors such as the choice of the message key not being totally random – they sometimes opted for obvious keys (three successive letters) or they made the mistake of repeating the same key (for example, the initials of their name). There were also the security measures taken by those responsible for creating the notebooks with the daily key settings: they did not allow any rotor to repeat the position from one day to another, and no letter of the plugboard was replaced by its neighbouring letters. These measures, paradoxically, greatly reduced the total number of possible configurations and provided shortcuts to cryptanalysts. In addition, sometimes the Allies managed to obtain a notebook of key settings, which gave the analysts a boost from which to continue advancing. Without these external factors, one wonders whether the Allied cryptologists could have deciphered the Enigma.
By Miguel Barral for Ventana al Conocimiento
@migbarral
Source: OpenMind